-->
A HealthVault application uses a private key to encrypt the first handshake message that it sends to the platform service. HealthVault then uses a public key to verify the sender. The public key must be registered with HealthVault through the Application Configuration Center. The private key is securely stored by the application and is never shared with HealthVault.
Apr 05, 2018 From the top-level in IIS Manager, select “Server Certificates”. Then click the “Create” on the right. This will create a self-signed certificate valid for a year with a private key.
Best practices
Theft of the private key will allow an unauthorized agent to impersonate your application and make calls to HealthVault.
- Store it somewhere safe.
- Do not include it in any e-mail messages.
- Limit access to the key to only those people who must have access.
Creating the key pair
Windows includes a couple of ways to generate a HealthVault compatible X509 certificate.
If you lose the certificate in the future, or if you generated your private key in a different way, you can export a DER-encoded public certificate using the Microsoft Management Console. The corresponding private key is wrapped in a certificate that has been installed in your LocalMachineMy store.
To create the private/public key pair:
Powershell Export Private Key Pem
In Windows 10/Server 2016
- Open PowerShell as an Administrator
- Paste the following content into PowerShell, replacing “Insert your ApplicationID here” with the ApplicationID you received from HealthVault’s Application Configuration Center.
On previous versions of Windows
- Open a Visual Studio Developer Command Prompt as an Administrator.
- Execute the following command, replacing this GUID with your own application ID:
These commands will install the private key on your machine and write the public key to the specified certificate file. You will find the signed certificate in the Downloads folder for the currently logged in user.
Exporting your private key and installing it on your application server
Once the CER has been uploaded and associated with your application, install the PFX on your application server(s).
To install the PFX:
Export Instructions (on machine where you generated the certificate):
- Use the Certificates MMC console, and open the folder containing the certificate. For information about opening the Certificates MMC console, see How to: View Certificates with the MMC Snap-in.
- Right-click your new certificate.
- From the context menu, select All Tasks>Export.
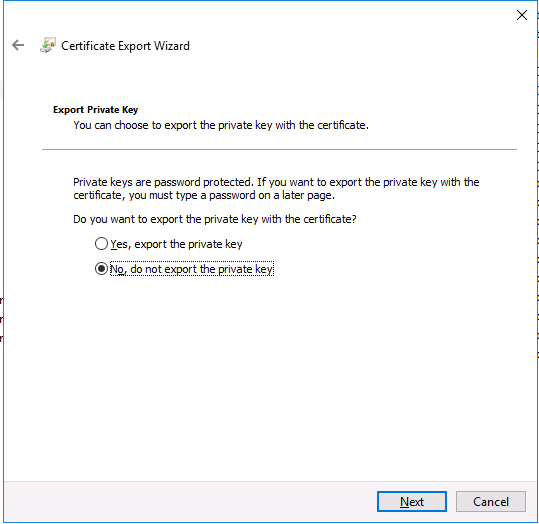
- Click Next
- Select Yes, Export the Private Key.
- Follow the remaining steps: Enter an output filename and choose a password to protect installation of this private key.
Import Instructions (on App server):
- Open the Certificates MMC console for the local machine.
- If the machine currently has a certificate with the same certificate name, delete the existing certificate before importing the new one.
- Under Certificates (Local Computer)Personal, right-click Certificates.
- Select All Tasks > Import.
- Use the file that you exported In Step 1.
- Select to load this cert into Personal.
Use WinHttpCertCfg to grant the NetworkService account the permission it needs to utilize this private key:
WinHttpCertCfg.exe -g -a NetworkService -c Local_MachineMy -s 'WildcatApp-<AppId>'
Deleting an old key
- Open the Certificates MMC console for the local machine store. For information about opening the Certificates MMC console, see How to: View Certificates with the MMC Snap-in.
- Open the Personal folder, and then open the Cetificates subfolder.
- Right-click the old certificate and select Delete.
Powershell Get Certificate
Old certificates are not cleanly deleted if a process currently has them open. You may need to shut off any web server instances that are currently running.