- A Ternary Fuzzy Extractor For Efficient Cryptographic Key Generation 3
- A Ternary Fuzzy Extractor For Efficient Cryptographic Key Generation X
- A Ternary Fuzzy Extractor For Efficient Cryptographic Key Generation 1
- A Ternary Fuzzy Extractor For Efficient Cryptographic Key Generation 2
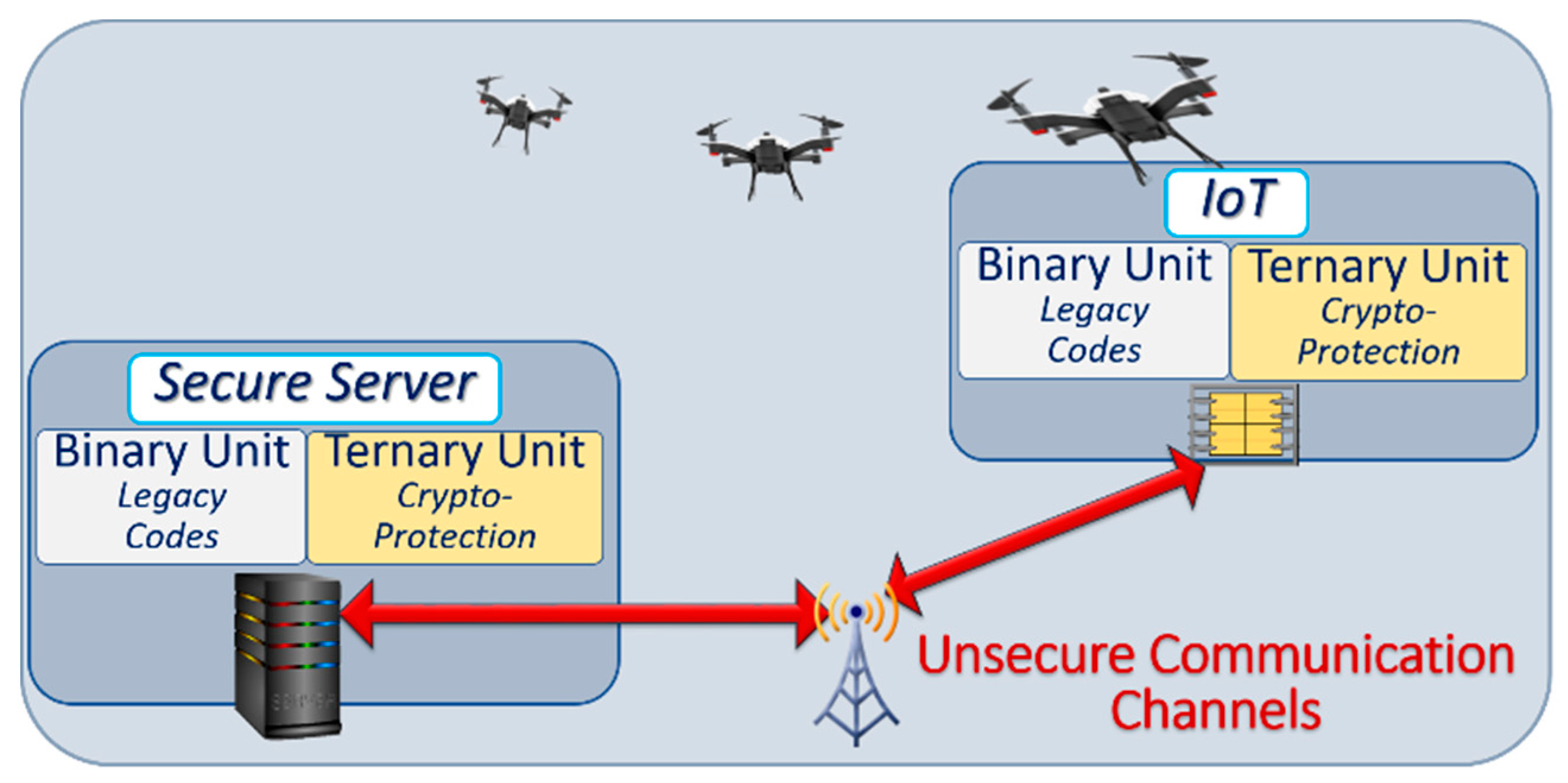
Fuzzy extractor structure using serially concatenated BCH-Polar codes is proposed to generate reproducible keys from a ReRAM-based ternary-state Physical Unclonable Functions (PUFs) for device authentication and secret key generation. The main concern in deploying PUF-based key generation methods is the leakage of information about. Fuzzy Extractors: How to Generate Strong Keys from Biometrics and Other Noisy Data∗ Yevgeniy Dodis† Rafail Ostrovsky‡ Leonid Reyzin§ Adam Smith¶ January 20, 2008 Abstract We provide formal definitions and efficient secure techniques for.turning noisy information into keys usable for any cryptographic application, and, in particular. A fuzzy extractor structure using serially concatenated BCH-Polar codes is proposed to generate reproducible keys from a ReRAM-based ternary-state Physical Unclonable Functions (PUFs) for device authentication and secret key generation. The main concern in deploying PUF-based key generation methods is the leakage of information about the secret keys from the publicly available helper data.
- Barker, E., & Kelsey, J. (2012). Recommendation for random number generation using deterministic random bit generators. NIST special publication 800-90A. http://csrc.nist.gov/publications/nistpubs/800-90A/SP800-90A.pdf.
- Berlekamp, E. (1965). On decoding binary Bose-Chadhuri-Hocquenghem codes. IEEE Transactions on Information Theory, 11(4), 577–579.MathSciNetCrossRefzbMATHGoogle Scholar
- Bogdanov, A., Knežević, M., Leander, G., Toz, D., Varici, K., & Verbauwhede, I. (2011). SPONGENT: a lightweight hash function. In Lecture notes in computer science (LNCS): Vol.6917. Workshop on cryptographic hardware and embedded systems—CHES 2011 (pp. 312–325). Berlin: Springer.CrossRefGoogle Scholar
- Bösch, C., Guajardo, J., Sadeghi, A.-R., Shokrollahi, J., & Tuyls, P. (2008). Efficient helper data key extractor on FPGAs. In Lecture notes in computer science (LNCS): Vol.5154. Workshop on cryptographic hardware and embedded systems—CHES 2008 (pp. 181–197). Berlin: Springer.CrossRefGoogle Scholar
- Burton, H. (1971). Inversionless decoding of binary BCH codes. IEEE Transactions on Information Theory, 17(4), 464–466.CrossRefzbMATHGoogle Scholar
- Carter, J. L., & Wegman, M. N. (1977). Universal classes of hash functions. In ACM symposium on theory of computing—STOC 1977 (pp. 106–112). New York: ACM.Google Scholar
- Chien, R. (1964). Cyclic decoding procedures for Bose-Chaudhuri-Hocquenghem codes. IEEE Transactions on Information Theory, 10(4), 357–363.MathSciNetCrossRefzbMATHGoogle Scholar
- Dodis, Y., Reyzin, L., & Smith, A. (2004). Fuzzy extractors: how to generate strong keys from biometrics and other noisy data. In Lecture notes in computer science (LNCS): Vol.3027. Advances in cryptology—EUROCRYPT 2004 (pp. 523–540). Berlin: Springer.CrossRefGoogle Scholar
- Dodis, Y., Ostrovsky, R., Reyzin, L., & Smith, A. (2008). Fuzzy extractors: how to generate strong keys from biometrics and other noisy data. SIAM Journal on Computing, 38(1), 97–139.MathSciNetCrossRefzbMATHGoogle Scholar
- Eastlake, D., Schiller, J., & Crocker, S. (2005). Randomness requirements for security. IETF RFC 4086. http://www.ietf.org/rfc/rfc4086.txt.
- Ferguson, N., & Schneier, B. (2003). Practical cryptography. New York: Wiley.Google Scholar
- Gallager, R. G. (1962). Low density parity-check codes. IRE Transactions on Information Theory, 8, 21–28.MathSciNetCrossRefzbMATHGoogle Scholar
- Guajardo, J., Kumar, S. S., Schrijen, G. J., & Tuyls, P. (2007). FPGA intrinsic PUFs and their use for IP protection. In Lecture notes in computer science (LNCS): Vol.4727. Workshop on cryptographic hardware and embedded systems—CHES 2007 (pp. 63–80). Berlin: Springer.CrossRefGoogle Scholar
- Gutmann, P. (2004). Cryptographic security architecture. Berlin: Springer.zbMATHGoogle Scholar
- Kelsey, J., Schneier, B., & Ferguson, N. (1999). Yarrow-160: notes on the design and analysis of the Yarrow cryptographic pseudorandom number generator. In Lecture notes in computer science (LNCS): Vol.1758. International workshop on selected areas in cryptography—SAC 1999 (pp. 13–33). Berlin: Springer.CrossRefGoogle Scholar
- Lenstra, A. K., Hughes, J. P., Augier, M., Bos, J. W., Kleinjung, T., & Wachter, C. (2012). Ron was wrong, Whit is right. Cryptology ePrint Archive, Report 2012/064.Google Scholar
- Linnartz, J.-P., & Tuyls, P. (2003). New shielding functions to enhance privacy and prevent misuse of biometric templates. In Lecture notes in computer science (LNCS): Vol.2688. International conference on audio- and video-based biometric person authentication—AVBPA 2003 (pp. 393–402). Berlin: Springer.CrossRefGoogle Scholar
- Maes, R., Tuyls, P., & Verbauwhede, I. (2009). Low-overhead implementation of a soft decision helper data algorithm for SRAM PUFs. In Lecture notes in computer science (LNCS): Vol.5747. Workshop on cryptographic hardware and embedded systems—CHES 2009 (pp. 332–347). Berlin: Springer.Google Scholar
- Maes, R., Tuyls, P., & Verbauwhede, I. (2009). Soft decision helper data algorithm for SRAM PUFs. In IEEE international symposium on information theory—ISIT 2009 (pp. 2101–2105). New York: IEEE.CrossRefGoogle Scholar
- Maes, R., Van Herrewege, A., & Verbauwhede, I. (2012). PUFKY: a fully functional PUF-based cryptographic key generator. In Lecture notes in computer science (LNCS): Vol.7428. Workshop on cryptographic hardware and embedded systems—CHES 2012. Berlin: Springer.Google Scholar
- Maiti, A., Casarona, J., McHale, L., & Schaumont, P. (2010). A large scale characterization of RO-PUF. In IEEE international symposium on hardware-oriented security and trust—HOST 2010 (pp. 94–99). New York: IEEE.CrossRefGoogle Scholar
- Massey, J. (1969). Shift-register synthesis and BCH decoding. IEEE Transactions on Information Theory, 15(1), 122–127.MathSciNetCrossRefzbMATHGoogle Scholar
- Nisan, N., & Zuckerman, D. (1996). Randomness is linear in space. Journal of Computer and System Sciences, 52(1), 43–52.MathSciNetCrossRefzbMATHGoogle Scholar
- Schnabl, G., & Bossert, M. (1995). Soft-decision decoding of Reed-Muller codes as generalized multiple concatenated codes. IEEE Transactions on Information Theory, 41(1), 304–308.CrossRefzbMATHGoogle Scholar
- Silverman, R., & Balser, M. (1954). Coding for constant-data-rate systems-part I. A new error-correcting code. Proceedings of the IRE, 42(9), 1428–1435.CrossRefGoogle Scholar
- Tarnovsky, C. (2010). Deconstructing a ‘Secure’ processor. Talk at Black Hat Federal 2010. http://www.blackhat.com/presentations/bh-dc-10/Tarnovsky_Chris/BlackHat-DC-2010-Tarnovsky-DASP-slides.pdf.
- Torrance, R., & James, D. (2009). The state-of-the-art in IC reverse engineering. In Lecture notes in computer science (LNCS): Vol.5747. Workshop on cryptographic hardware and embedded systems—CHES 2009 (pp. 363–381). Berlin: Springer.CrossRefGoogle Scholar
- Tuyls, P., & Batina, L. (2006). RFID-tags for anti-counterfeiting. In Lecture notes in computer science (LNCS): Vol.3860. Topics in cryptology: cryptographers’ track of the RSA conference—CT-RSA 2006 (pp. 115–131). Berlin: Springer.CrossRefGoogle Scholar
- Viterbi, A. (1967). Error bounds for convolutional codes and an asymptotically optimum decoding algorithm. IEEE Transactions on Information Theory, 13(2), 260–269.CrossRefzbMATHGoogle Scholar
- Yu, M.-D. M., M’Raihi, D., Sowell, R., & Devadas, S. (2011). Lightweight and secure PUF key storage using limits of machine learning. In Lecture notes in computer science (LNCS): Vol.6917. Workshop on cryptographic hardware and embedded systems—CHES 2011 (pp. 358–373). Berlin: Springer.CrossRefGoogle Scholar
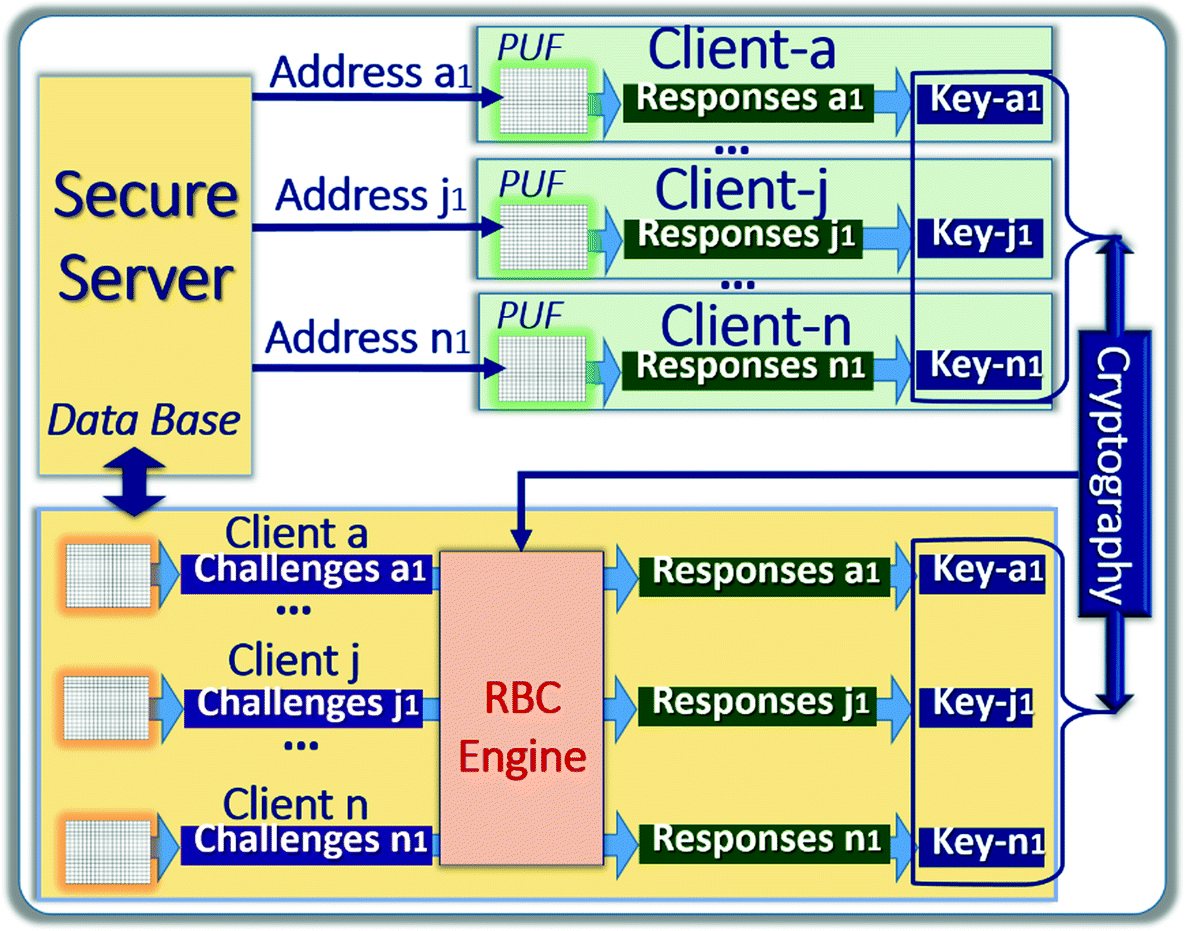
Cryptographic Key Generation from Physically Unclonable Functions Data
The following code is implemented in MatLab.
The generation procedure takes the PUF Data1 as input and generates the Key1 and helper data(which is totally random).The reproduction procedure takes the PUF Data2 and helper data as input and generates Key2.If Key1=Key2 both of the PUF's have been generated from the same device.
The input is taken to be random for now, but you should add your own PUF inputs here.
A Ternary Fuzzy Extractor For Efficient Cryptographic Key Generation 3
For the full project with test data input and analysis using PUF's, and more explanation and detailed working e-mail me atkaranahujax@gmail.com .

REFERENCES
Y. Dodis, R. Ostrovsky, L. Reyzin and A. Smith, “Fuzzy Extractors:How to Generate Strong Keys from Biometrics and Other Noisy Data,”(A preliminary version of this paper appeared in Eurocrypt 2004) SIAMJ. Comput., 38(1), pp. 97–139, 2008.
Hyunho Kang, Yohei Hori, Toshihiro Katashita, Manabu Hagiwara, Keiichi Iwamura,'Cryptographic Key Generation from PUF Data Using Efficient Fuzzy Extractors',2014
The MIT License (MIT)
Copyright (c) 2015
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the 'Software'), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
A Ternary Fuzzy Extractor For Efficient Cryptographic Key Generation X
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
A Ternary Fuzzy Extractor For Efficient Cryptographic Key Generation 1
A Ternary Fuzzy Extractor For Efficient Cryptographic Key Generation 2
THE SOFTWARE IS PROVIDED 'AS IS', WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.